Our technicians and their favorite tools
Our IT specialist Robert presents Pangolin.
Brief information about Pangolin
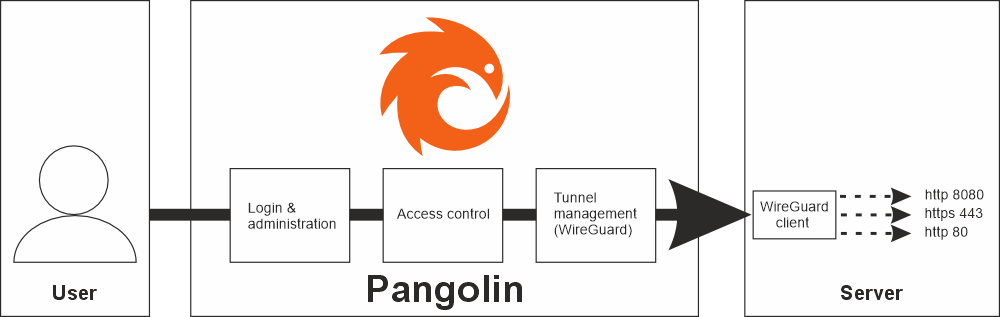
Pangolin is open-source software that functions as a tunneled reverse proxy.
The tool allows services in a private or internal network to be made accessible via the Internet without having to expose classic public ports such as 80 or 443 for Web or 25 for email via DynDNS or even setting up remote VPN connections.
Pangolin places particular emphasis on identity and access controls (identity-aware access control) and high availability.

Functions of Pangolin
1. Tunneling instead of traditional ports
Normally, web or application services in a home or company network would be made accessible via a publicly accessible server or router with open ports. This has two disadvantages: firstly, public access is a potential point of attack; secondly, the network (e.g., through CGNAT or firewalls) may be set up in such a way that hardly anything is accessible from the outside. Pangolin circumvents this by establishing a “tunnel” from the inside (e.g., an endpoint in the private network) to an external, available node. Data traffic is routed through this network. This means that no public ports need to be opened in the internal network.
2. Reverse proxy with identity verification
A reverse proxy forwards incoming requests to an internal service. Pangolin extends this: every access is checked against authentication and authorization rules before being forwarded – in other words, not just according to the motto “is the service accessible,” but “is the user even allowed to access this service?” Single sign-on (SSO), multi-factor authentication (MFA), access conditions such as IP address range or geolocation, etc. can be used for this check.
3. Central management via dashboard
The software provides a dashboard (user interface) for managing connected “sites” (networks), resources (services), access rules, domains, etc. This provides a central point of control.
4. Self-hosting and cloud options
You can either host Pangolin yourself (i.e., install it on your own server or VPS) or use a cloud service version. This offers flexibility depending on your technical equipment and requirements.
What else is possible with Pangolin
Pangolin goes beyond basic functions and offers additional features and application scenarios—here are some important examples:
Versatile access controls
In addition to user names and passwords, PIN codes, temporary links (self-destructing links), geographic restrictions, and IP filters are also possible. This allows for very fine-grained access control.
Support for various transport protocols
Not only HTTP/HTTPS – Pangolin also supports raw TCP and UDP connections through tunneling technology, which can be important for special services.
Use in home networks, IoT, and edge environments
If you have a device at home that you want to access from outside—for example, a media server, a camera, or individual smart home components—Pangolin can help without opening up your home network or exposing it to many security risks. Users report, for example:
“Installed in a small VPS ... as an entry point for all the services I want to expose to friends and family from my homelab (dynamic IP), completely secure and very easy to manage.”
Integration with identity systems & single sign-on
Pangolin can be linked to identity providers such as OAuth2/OIDC (e.g., authentik) or SSO solutions, allowing access via existing user directories.
Visibility & analytics
The dashboard provides insight into metrics, health checks, and connection status—important for monitoring and securing services.
Branding & domains
Pangolin offers options for using your own domains, subdomains, and customizing branding, etc.—you can design access to match your own look and feel.
Conclusion
Pangolin is a modern tool that overcomes the classic limitations of reverse proxies and VPN solutions: it allows secure, controlled access to internal or distributed services—without open ports, with identity verification and high availability.
This makes it ideal for users like our expert Robert, who hosts such services himself or manages distributed networks. However, if you only want to operate a very simple public service and have no special security requirements, you should consider whether this additional effort is justified.