Enabling automatic security updates on Linux
How to activate automatic security updates using the Debian/Ubuntu operating systems with Linux.
Security updates under Linux
Linux’s security updates are packages and system component updates that patch a security hole or improve the robustness of the system. Some of those updates are quite critical and should be applied almost immediately to protect your server from severe vulnerabilities such as the recently discovered Log4J exploit.
With Linux increased popularity, especially as a server platform, it has become one of the main targets for security attacks. This means you should keep your server’s security profile in shape to avoid it being compromised. It also means regular backups are a must.
Linux’s package management utility (apt in our case because Debian and its derivates rely on it) can be programmed to check for, and automatically install, security patches and updates.
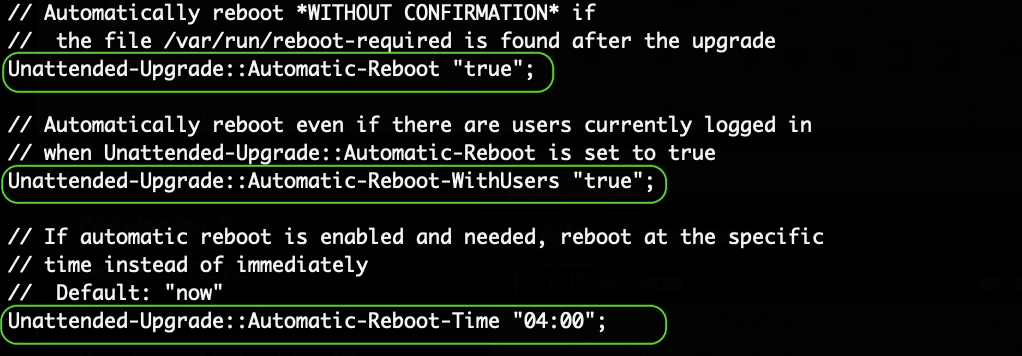
APT can also send you email alerts about such updates and even reboot the system after installing packages that require a restart, such as newer Kernels.
This feature of APT is called Unattended Upgrades. It installs and runs as a Daemon (background system service) and it is relatively easy to configure. Here is a brief how to…
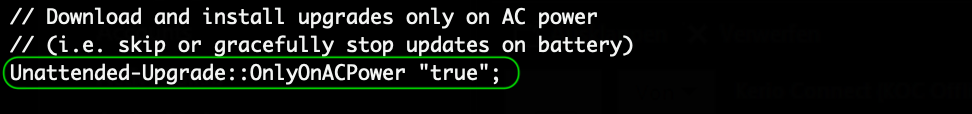
Optional: Configure automatic upgrades to run only on AC power
This is useful in environments where the server relies on a UPS. To avoid the UPS running out of power and the upgrade process getting interrupted, which might cause some issues that you will need to fix, set the process to
* Please note that, for the above function to work properly, you will need the relevant UPS management package installed. For APC UPS units you can install the apcupsd package with;
$ apt-get install apcupsd
For other UPS units, please check with the unit manufacturer or check unit compatibility with the Open-Source Network UPS Tools (NUT)
Finally, let’s backup and edit the auto upgrades intervals configuration file;
$ cp /etc/apt/apt.conf.d/20auto-upgrades /etc/apt/apt.conf.d/20auto-upgrades.BACKUP-$(date '+%Y-%m-%d')$ nano /etc/apt/apt.conf.d/20auto-upgrades
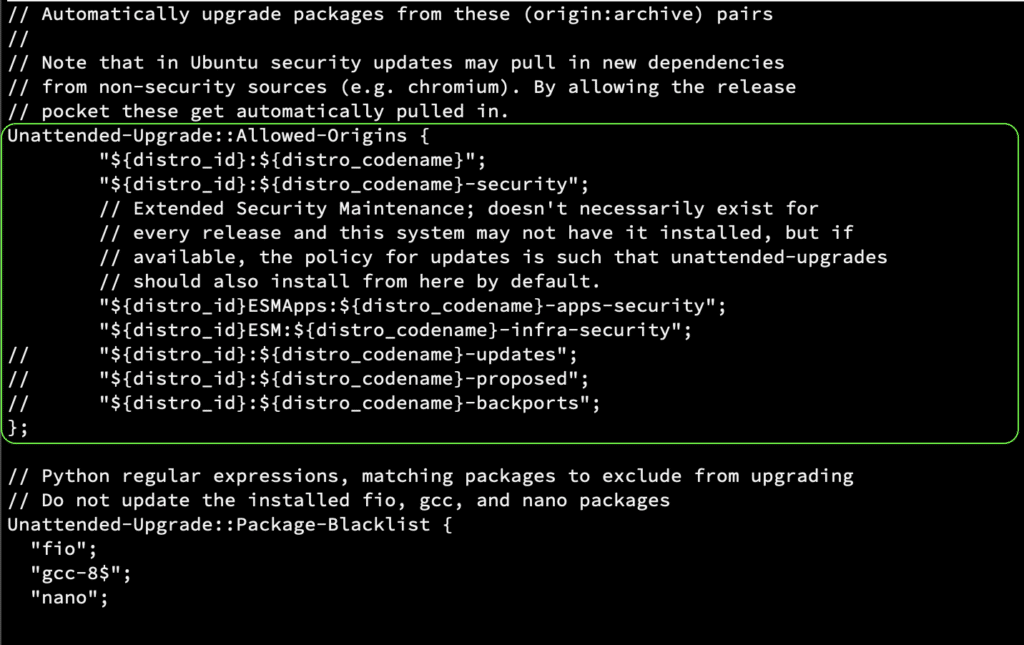
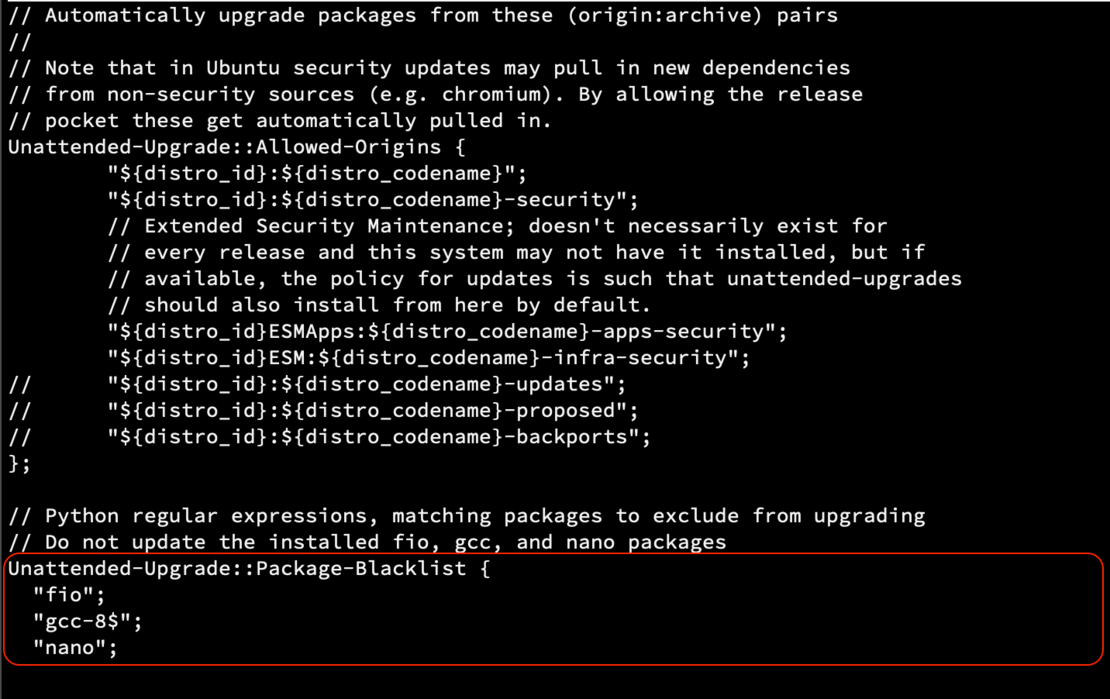
Delete any existing content then paste the following lines:
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";
APT::Periodic::AutocleanInterval "30";
The above three lines translate to:
Check for new updates every “1” days
Run unattended upgrade every “1” days
Delete cached APT files every “30” days
You should adjust those values to best suite your server/environment.
Do a dry run test!
We are done. Now, let’s do a dry run with the new configurations to make sure it will execute without errors. In your Terminal do:
$ unattended-upgrades --dry-run --debug
Make sure the dry run does not fail with an error message.
Check the auto upgrade log to see if there are any serious errors during the dry run by doing;
$ cat /var/log/unattended-upgrades/unattended-upgrades.log | grep -i error
You can safely ignore any “ERROR Lock could not be acquired” instances. This simply means there was another APT process running in the background during your dry run.
If all goes well you can exit the shell and wait for the scheduled auto update to run on its own. Refer to the log to make sure all went fine. If you have configured the email function you should be notified either way.
Tip: One of the best practices to improve your Linux server security is to refrain from installing unnecessary packages. Install just the bare minimum that is required for your server to function properly. The more packages you accumulate the more vulnerable your server is going to be.
If you need to test something test it locally. Check the CVE database to make sure it is ready for launching before you deploy it on your online server. When deploying it, make sure you follow the developer’s recommended security procedures and enable the minimum amount of required firewall ports for it.